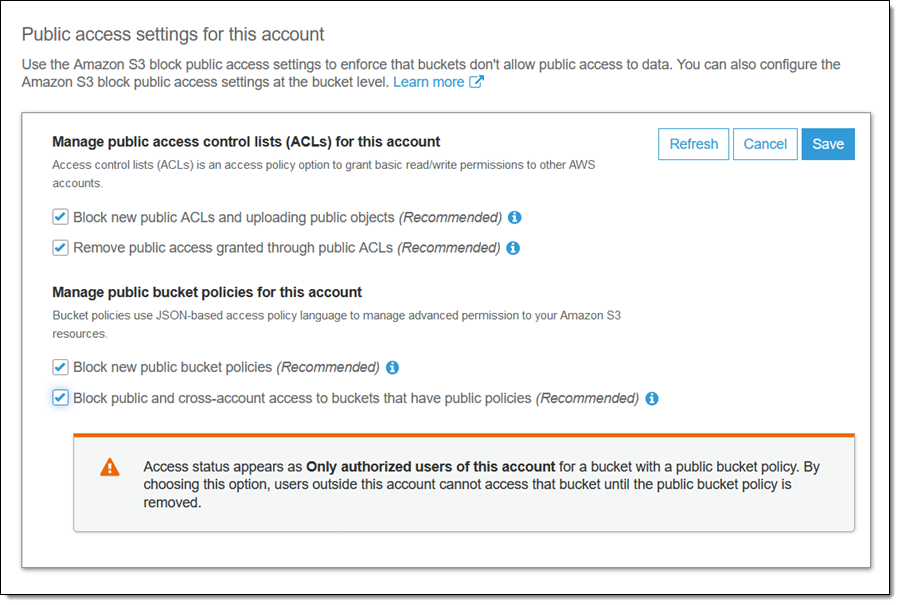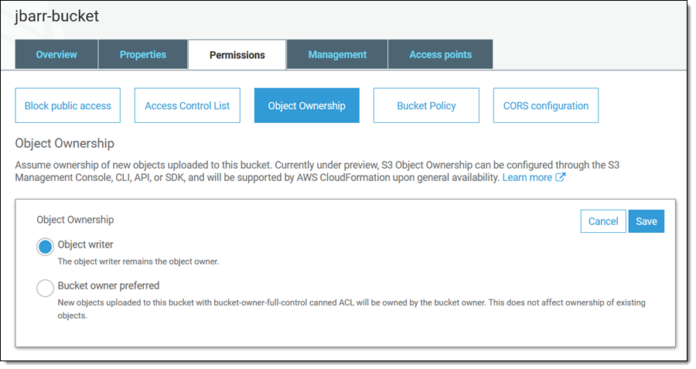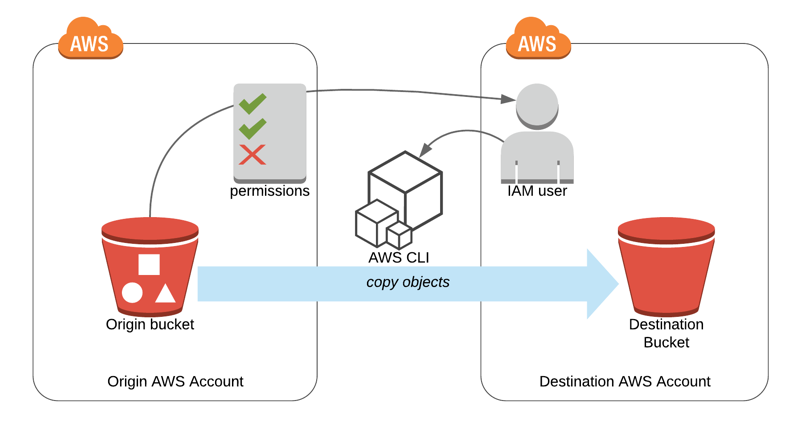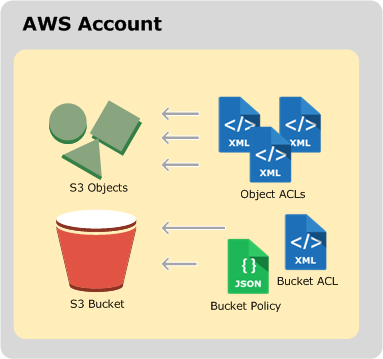
Bucket Sharing Tutorial. How to share Amazon S3 Bucket with another AWS Account. How to grant access to your bucket.

Amazon S3 Bucket Policies. How to configure Amazon S3 Bucket Policies. Examples of Bucket Policies. How to apply Amazon S3 Buckets Policies. View, Edit, Delete Amazon S3 Bucket Policies.

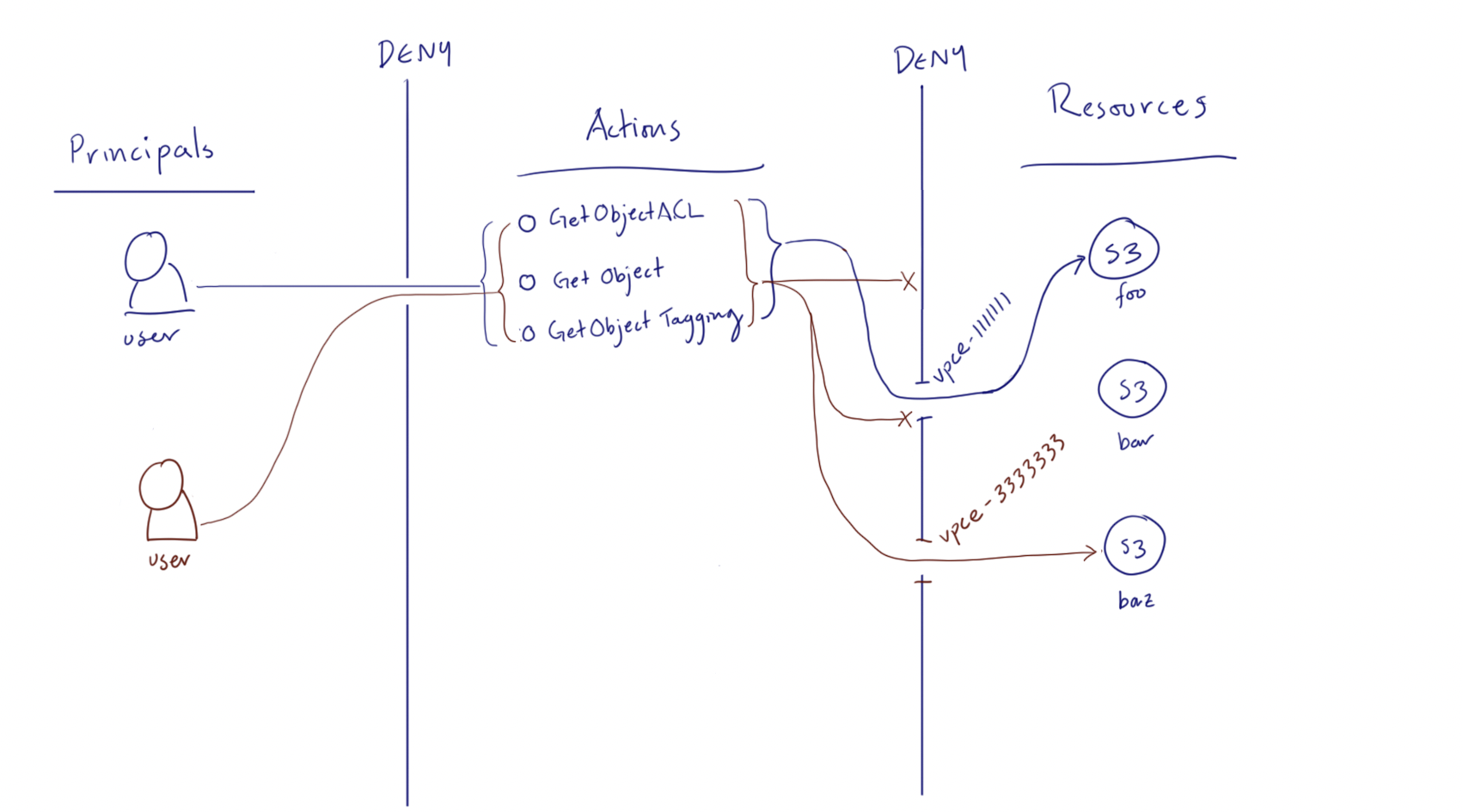
Example Scenarios for AWS Config Continuous Monitoring of Amazon S3 Bucket Access Controls | AWS Management & Governance Blog

IAM Policies and Bucket Policies and ACLs! Oh, My! (Controlling Access to S3 Resources) | AWS Security Blog